 Multiple Exceptions (user mode) - Modeling Example
Multiple Exceptions (user mode) - Modeling Example Multiple Exceptions (kernel mode)
Multiple Exceptions (kernel mode) Multiple Exceptions (managed space)
Multiple Exceptions (managed space)- Multiple Exceptions (stowed)
 Dynamic Memory Corruption (process heap)
Dynamic Memory Corruption (process heap) Dynamic Memory Corruption (kernel pool)
Dynamic Memory Corruption (kernel pool)- Dynamic Memory Corruption (managed heap)
 False Positive Dump
False Positive Dump Lateral Damage (general)
Lateral Damage (general)- Lateral Damage (CPU mode)
 Optimized Code (function parameter reuse)
Optimized Code (function parameter reuse) Invalid Pointer (general)
Invalid Pointer (general)- Invalid Pointer (objects)
 NULL Pointer (code)
NULL Pointer (code) NULL Pointer (data)
NULL Pointer (data) Inconsistent Dump
Inconsistent Dump Hidden Exception (user space)
Hidden Exception (user space)- Hidden Exception (kernel space)
- Hidden Exception (managed space)
 Deadlock (critical sections)
Deadlock (critical sections) Deadlock (executive resources)
Deadlock (executive resources) Deadlock (mixed objects, user space)
Deadlock (mixed objects, user space) Deadlock (LPC)
Deadlock (LPC) Deadlock (mixed objects, kernel space)
Deadlock (mixed objects, kernel space) Deadlock (self)
Deadlock (self)- Deadlock (managed space)
- Deadlock (.NET Finalizer)
 Changed Environment
Changed Environment Incorrect Stack Trace
Incorrect Stack Trace OMAP Code Optimization
OMAP Code Optimization No Component Symbols
No Component Symbols Insufficient Memory (committed memory)
Insufficient Memory (committed memory) Insufficient Memory (handle leak)
Insufficient Memory (handle leak) Insufficient Memory (kernel pool)
Insufficient Memory (kernel pool) Insufficient Memory (PTE)
Insufficient Memory (PTE) Insufficient Memory (module fragmentation)
Insufficient Memory (module fragmentation) Insufficient Memory (physical memory)
Insufficient Memory (physical memory) Insufficient Memory (control blocks)
Insufficient Memory (control blocks)- Insufficient Memory (reserved virtual memory)
- Insufficient Memory (session pool)
- Insufficient Memory (stack trace database)
- Insufficient Memory (region)
- Insufficient Memory (stack)
 Spiking Thread
Spiking Thread Module Variety
Module Variety Stack Overflow (kernel mode)
Stack Overflow (kernel mode) Stack Overflow (user mode)
Stack Overflow (user mode) Stack Overflow (software implementation)
Stack Overflow (software implementation)- Stack Overflow (insufficient memory)
- Stack Overflow (managed space)
 Managed Code Exception
Managed Code Exception- Managed Code Exception (Scala)
- Managed Code Exception (Python)
 Truncated Dump
Truncated Dump Waiting Thread Time (kernel dumps)
Waiting Thread Time (kernel dumps) Waiting Thread Time (user dumps)
Waiting Thread Time (user dumps) Memory Leak (process heap) - Modeling Example
Memory Leak (process heap) - Modeling Example Memory Leak (.NET heap)
Memory Leak (.NET heap)- Memory Leak (page tables)
- Memory Leak (I/O completion packets)
- Memory Leak (regions)
 Missing Thread
Missing Thread Unknown Component
Unknown Component Double Free (process heap)
Double Free (process heap) Double Free (kernel pool)
Double Free (kernel pool) Coincidental Symbolic Information
Coincidental Symbolic Information Stack Trace
Stack Trace- Stack Trace (I/O request)
- Stack Trace (file system filters)
- Stack Trace (database)
- Stack Trace (I/O devices)
 Virtualized Process (WOW64)
Virtualized Process (WOW64) Stack Trace Collection (unmanaged space)
Stack Trace Collection (unmanaged space)- Stack Trace Collection (managed space)
- Stack Trace Collection (predicate)
- Stack Trace Collection (I/O requests)
- Stack Trace Collection (CPUs)
 Coupled Processes (strong)
Coupled Processes (strong) Coupled Processes (weak)
Coupled Processes (weak) Coupled Processes (semantics)
Coupled Processes (semantics) High Contention (executive resources)
High Contention (executive resources) High Contention (critical sections)
High Contention (critical sections) High Contention (processors)
High Contention (processors)- High Contention (.NET CLR monitors)
- High Contention (.NET heap)
- High Contention (sockets)
 Accidental Lock
Accidental Lock Passive Thread (user space)
Passive Thread (user space) Passive System Thread (kernel space)
Passive System Thread (kernel space) Main Thread
Main Thread Busy System
Busy System Historical Information
Historical Information Object Distribution Anomaly (IRP)
Object Distribution Anomaly (IRP)- Object Distribution Anomaly (.NET heap)
 Local Buffer Overflow (user space)
Local Buffer Overflow (user space)- Local Buffer Overflow (kernel space)
 Early Crash Dump
Early Crash Dump Hooked Functions (user space)
Hooked Functions (user space) Hooked Functions (kernel space)
Hooked Functions (kernel space)- Hooked Modules
 Custom Exception Handler (user space)
Custom Exception Handler (user space) Custom Exception Handler (kernel space)
Custom Exception Handler (kernel space) Special Stack Trace
Special Stack Trace Manual Dump (kernel)
Manual Dump (kernel) Manual Dump (process)
Manual Dump (process) Wait Chain (general)
Wait Chain (general) Wait Chain (critical sections)
Wait Chain (critical sections) Wait Chain (executive resources)
Wait Chain (executive resources) Wait Chain (thread objects)
Wait Chain (thread objects) Wait Chain (LPC/ALPC)
Wait Chain (LPC/ALPC) Wait Chain (process objects)
Wait Chain (process objects) Wait Chain (RPC)
Wait Chain (RPC) Wait Chain (window messaging)
Wait Chain (window messaging) Wait Chain (named pipes)
Wait Chain (named pipes)- Wait Chain (mutex objects)
- Wait Chain (pushlocks)
- Wait Chain (CLR monitors)
- Wait Chain (RTL_RESOURCE)
- Wait Chain (modules)
- Wait Chain (nonstandard synchronization)
- Wait Chain (C++11, condition variable)
- Wait Chain (SRW lock)
 Corrupt Dump
Corrupt Dump Dispatch Level Spin
Dispatch Level Spin No Process Dumps
No Process Dumps No System Dumps
No System Dumps Suspended Thread
Suspended Thread Special Process
Special Process Frame Pointer Omission
Frame Pointer Omission False Function Parameters
False Function Parameters Message Box
Message Box Self-Dump
Self-Dump Blocked Thread (software)
Blocked Thread (software) Blocked Thread (hardware)
Blocked Thread (hardware)- Blocked Thread (timeout)
 Zombie Processes
Zombie Processes Wild Pointer
Wild Pointer Wild Code
Wild Code Hardware Error
Hardware Error Handle Limit (GDI, kernel space)
Handle Limit (GDI, kernel space)- Handle Limit (GDI, user space)
 Missing Component (general)
Missing Component (general) Missing Component (static linking, user mode)
Missing Component (static linking, user mode) Execution Residue (unmanaged space, user)
Execution Residue (unmanaged space, user)- Execution Residue (unmanaged space, kernel)
- Execution Residue (managed space)
 Optimized VM Layout
Optimized VM Layout- Invalid Handle (general)
- Invalid Handle (managed space)
- Overaged System
- Thread Starvation (realtime priority)
- Thread Starvation (normal priority)
- Duplicated Module
- Not My Version (software)
- Not My Version (hardware)
- Data Contents Locality
- Nested Exceptions (unmanaged code)
- Nested Exceptions (managed code)
- Affine Thread
- Self-Diagnosis (user mode)
- Self-Diagnosis (kernel mode)
- Self-Diagnosis (registry)
- Inline Function Optimization (unmanaged code)
- Inline Function Optimization (managed code)
- Critical Section Corruption
- Lost Opportunity
- Young System
- Last Error Collection
- Hidden Module
- Data Alignment (page boundary)
- C++ Exception
- Divide by Zero (user mode)
- Divide by Zero (kernel mode)
- Swarm of Shared Locks
- Process Factory
- Paged Out Data
- Semantic Split
- Pass Through Function
- JIT Code (.NET)
- JIT Code (Java)
- Ubiquitous Component (user space)
- Ubiquitous Component (kernel space)
- Nested Offender
- Virtualized System
- Effect Component
- Well-Tested Function
- Mixed Exception
- Random Object
- Missing Process
- Platform-Specific Debugger
- Value Deviation (stack trace)
- Value Deviation (structure field)
- Runtime Thread (CLR)
- Runtime Thread (Python, Linux)
- Coincidental Frames
- Fault Context
- Hardware Activity
- Incorrect Symbolic Information
- Message Hooks - Modeling Example
- Coupled Machines
- Abridged Dump
- Exception Stack Trace
- Distributed Spike
- Instrumentation Information
- Template Module
- Invalid Exception Information
- Shared Buffer Overwrite
- Pervasive System
- Problem Exception Handler
- Same Vendor
- Crash Signature
- Blocked Queue (LPC/ALPC)
- Fat Process Dump
- Invalid Parameter (process heap)
- Invalid Parameter (runtime function)
- String Parameter
- Well-Tested Module
- Embedded Comment
- Hooking Level
- Blocking Module
- Dual Stack Trace
- Environment Hint
- Top Module
- Livelock
- Technology-Specific Subtrace (COM interface invocation)
- Technology-Specific Subtrace (dynamic memory)
- Technology-Specific Subtrace (JIT .NET code)
- Technology-Specific Subtrace (COM client call)
- Dialog Box
- Instrumentation Side Effect
- Semantic Structure (PID.TID)
- Directing Module
- Least Common Frame
- Truncated Stack Trace
- Data Correlation (function parameters)
- Data Correlation (CPU times)
- Module Hint
- Version-Specific Extension
- Cloud Environment
- No Data Types
- Managed Stack Trace
- Managed Stack Trace (Scala)
- Managed Stack Trace (Python)
- Coupled Modules
- Thread Age
- Unsynchronized Dumps
- Pleiades
- Quiet Dump
- Blocking File
- Problem Vocabulary
- Activation Context
- Stack Trace Set
- Double IRP Completion
- Caller-n-Callee
- Annotated Disassembly (JIT .NET code)
- Annotated Disassembly (unmanaged code)
- Handled Exception (user space)
- Handled Exception (.NET CLR)
- Handled Exception (kernel space)
- Duplicate Extension
- Special Thread (.NET CLR)
- Hidden Parameter
- FPU Exception
- Module Variable
- System Object
- Value References
- Debugger Bug
- Empty Stack Trace
- Problem Module
- Disconnected Network Adapter
- Network Packet Buildup
- Unrecognizable Symbolic Information
- Translated Exception
- Regular Data
- Late Crash Dump
- Blocked DPC
- Coincidental Error Code
- Punctuated Memory Leak
- No Current Thread
- Value Adding Process
- Activity Resonance
- Stored Exception
- Spike Interval
- Stack Trace Change
- Unloaded Module
- Deviant Module
- Paratext
- Incomplete Session
- Error Reporting Fault
- First Fault Stack Trace
- Frozen Process
- Disk Packet Buildup
- Hidden Process
- Active Thread (Mac OS X)
- Active Thread (Windows)
- Critical Stack Trace
- Handle Leak
- Module Collection
- Module Collection (predicate)
- Deviant Token
- Step Dumps
- Broken Link
- Debugger Omission
- Glued Stack Trace
- Reduced Symbolic Information
- Injected Symbols
- Distributed Wait Chain
- One-Thread Process
- Module Product Process
- Crash Signature Invariant
- Small Value
- Shared Structure
- Thread Cluster
- False Effective Address
- Screwbolt Wait Chain
- Design Value
- Hidden IRP
- Tampered Dump
- Memory Fluctuation (process heap)
- Last Object
- Rough Stack Trace (unmanaged space)
- Rough Stack Trace (managed space)
- Past Stack Trace
- Ghost Thread
- Dry Weight
- Exception Module
- Reference Leak
- Origin Module
- Hidden Call
- Corrupt Structure
- Software Exception
- Crashed Process
- Variable Subtrace
- User Space Evidence
- Internal Stack Trace
- Distributed Exception (managed code)
- Thread Poset
- Stack Trace Surface
- Hidden Stack Trace
- Evental Dumps
- Clone Dump
- Parameter Flow
- Critical Region
- Diachronic Module
- Constant Subtrace
- Not My Thread
- Window Hint
- Place Trace
- Stack Trace Signature
- Relative Memory Leak
- Quotient Stack Trace
- Module Stack Trace
- Foreign Module Frame
- Unified Stack Trace
- Mirror Dump Set
- Memory Fibration
- Aggregated Frames
- Frame Regularity
- Stack Trace Motif
- System Call
- Stack Trace Race
- Hyperdump
- Disassembly Ambiguity
- Exception Reporting Thread
- Active Space
- Subsystem Modules
- Region Profile
- Region Clusters
- Source Stack Trace
- Hidden Stack
- Interrupt Stack
- False Memory
- Frame Trace
- Pointer Cone
- Context Pointer
- Pointer Class
- False Frame
- Procedure Call Chain
- C++ Object
- COM Exception
- Structure Sheaf
- Saved Exception Context (.NET)
- Shared Thread
- Spiking Interrupts
- Structure Field Collection
- Black Box
- Rough Stack Trace Collection (unmanaged space)
- COM Object
- Shared Page
- Exception Collection
- Dereference Nearpoint
- Address Representations
- Near Exception
- Shadow Stack Trace
- Past Process
- Foreign Stack
- Annotated Stack Trace
- Disassembly Summary
- Region Summary
- Analysis Summary
- Region Spectrum
- Normalized Region
Structural and Behavioral Patterns for Diagnostics, Anomaly Detection, Forensics, Prognostics, Root Cause Analysis, Debugging
Our tools are only as good as our pattern language.

Analysis patterns for the quality of software diagnostics in endpoint devices, enterprise, and cloud environments.
Diagnostics Science
Diagnostics is the mother of problem solving.
All areas of human activity involve the use of diagnostics. Proper diagnostics identifies the right problems to solve. We are now a part of a non-profit organization dedicated to the developing and promoting the application of such diagnostics: systemic and pattern-oriented (pattern-driven and pattern-based).
The Software Diagnostics and Anomaly Detection Group
Please join LinkedIn The Software Diagnostics and Anomaly Detection Group.
Memory Dump Analysis Anthology, Volume 16
Available in PDF format from Software Diagnostics Services
This reference volume consists of revised, edited, cross-referenced, and thematically organized selected articles from Software Diagnostics Institute (DumpAnalysis.org + TraceAnalysis.org) and Software Diagnostics Library (former Crash Dump Analysis blog, DumpAnalysis.org/blog) about software diagnostics, root cause analysis, debugging, crash and hang dump analysis, software trace and log analysis written from 15 April 2023 to 14 April 2024 for software engineers developing and maintaining products on Windows platforms, quality assurance engineers testing software, technical support, DevOps and DevSecOps, escalation and site reliability engineers dealing with complex software issues, security and vulnerability researchers, reverse engineers, malware and memory forensics analysts. This volume is fully cross-referenced with volumes 1 – 15 and features:
- 19 new crash dump analysis patterns
- 13 new software trace and log analysis patterns
- New defect mechanism pattern
- Introduction to Lov language
- Lists of recommended books
Product information:
- Title: Memory Dump Analysis Anthology, Volume 16
- Authors: Dmitry Vostokov, Software Diagnostics Institute
- Language: English
- Product Dimensions: 22.86 x 15.24
- Paperback: 170 pages
- Publisher: OpenTask (April 2024)
- ISBN-13: 978-1-912636-16-7

Advanced Software Diagnostics and Debugging Reference
These volumes are now also called Diagnomicon!
The new Volume 16 brings the total number of books to 18.
Now includes the new Revised Edition of Volume 1, Revised Edition of Volume 2, Revised Edition of Volume 3, Revised Edition of Volume 4, and Revised Edition of Volume 5.
Memory Dump Analysis Anthology contains revised, edited, cross-referenced, and thematically organized selected articles from Software Diagnostics Institute and Software Diagnostics Library (former Crash Dump Analysis blog) about software diagnostics, debugging, crash dump analysis, software trace and log analysis, malware analysis, and memory forensics. Its 16 volumes in 18 books have more than 5,400 pages and, among many topics, include more than 440 memory analysis patterns (mostly for WinDbg Windows debugger with selected macOS and Linux GDB variants), more than 70 WinDbg case studies, and more than 240 general trace and log analysis patterns. In addition, there are three supplemental volumes with articles reprinted in full color.
Tables of Contents and Indexes of WinDbg Commands from all volumes
Click on an individual volume to see its description and table of contents:
You can buy the 16-volume set from Software Diagnostics Services with a discount and also get free access to Software Diagnostics Library.
Praise for the series:
I have been working with reversing, dumps, IAT, unpacking, etc. and I am one of the few at my workplace that like analyzing hangs and crashes. I always knew that I had more to learn. So I continuously look for more info. Many links directed me to dumpanalysis.org. Frankly speaking, its spartan/simple design made me question its seriousness. But after reading some articles, I immediately decided to order "Memory Dump Analysis Anthology". I have only read 100 pages so far. But I am stunned. It is such an amazing book. How the author refines/reconstructs the call stack, and finds useful information in the stack is incredible. I am enormously thankful for the effort that the author has put into making these books. They are very didactic even though the topic is a bit hard. It is a real treasure.
Mattias Hogstrom
Book: Advanced Windows Memory Dump Analysis with Data Structures, Fifth Edition
Available in PDF format from Software Diagnostics Technology and Services.
The full transcript of the Software Diagnostics Services training course with 16 step-by-step exercises, notes, and selected questions and answers. Learn how to navigate through memory dump space and Windows data structures to diagnose, troubleshoot, and debug complex software incidents. The training uses a unique and innovative pattern-oriented analysis approach to speed up the learning curve. It consists of practical step-by-step exercises using WinDbg to diagnose structural and behavioral patterns in the 64-bit kernel and complete (physical) memory dumps. Additional topics include memory search, kernel linked list navigation, practical WinDbg scripting, registry, system variables and objects, device drivers, and I/O. Prerequisites are basic and intermediate level Windows memory dump analysis: the ability to list processors, processes, threads, modules, apply symbols, walk through stack traces and raw stack data, diagnose patterns such as heap corruption, CPU spike, memory leaks, access violation, wait chains and deadlocks. If you don't feel comfortable with prerequisites, then Accelerated Windows Memory Dump Analysis training book is recommended before purchasing and reading this book course. Audience: Software technical support and escalation engineers, system administrators, security researchers, reverse engineers, malware and memory forensics analysts, software developers, and quality assurance engineers. The fifth edition uses the latest WinDbg, includes the relevant Unified Modeling Language tutorial, revised and extended existing exercises, and added the exercise that demonstrates the use of a Generative AI LLM assistant.
- Title: Advanced Windows Memory Dump Analysis with Data Structures: Training Course Transcript and WinDbg Practice Exercises with Notes, Fifth Edition
- Authors: Dmitry Vostokov, Software Diagnostics Services, Dublin School of Security
- Publisher: OpenTask (March 2024)
- Language: English
- Product Dimensions: 28.0 x 21.6
- Paperback: 341 pages
- ISBN-13: 978-1912636952

Theoretical Software Diagnostics, Fourth Edition
The following direct links can be used to order the fourth edition of the book:
Available in PDF format from Software Diagnostics Technology and Services
Contains reprinted articles in full color (including more than 230 figures) from 16 volumes of Memory Dump Analysis Anthology (Diagnomicon) related to pattern-oriented software diagnostics with additional comments showing the historical development of this autonomous and distinctive discipline over the last 18 years. In addition to 15 new articles, the fourth edition includes updated threads of thinking, a list of mathematical concepts, and notes’ references, and was completely remastered.
Product information:
- Title: Theoretical Software Diagnostics: Collected Articles, Fourth Edition
- Authors: Dmitry Vostokov, Software Diagnostics Institute
- Language: English
- Product Dimensions: 21.6 x 14.0
- PDF: 398 pages
- Publisher: OpenTask (February 2024)
- ISBN-13: 978-1912636914
Table of Contents
Bird's-eye View of Pages
Online Training: Advanced Windows Memory Dump Analysis with Data Structures
Software Diagnostics Services organizes this online training course.

TBD
Learn how to navigate through memory dump space and Windows data structures to diagnose, troubleshoot, and debug complex software incidents. The training uses a unique and innovative pattern-oriented analysis approach to speed up the learning curve. It consists of 15 practical step-by-step exercises using WinDbg to diagnose structural and behavioral patterns in the 64-bit kernel and complete (physical) memory dumps. Additional topics include memory search, kernel linked list navigation, practical WinDbg scripting including built-in language and JavaScript, registry, system variables and objects, device drivers, I/O, file system filters, and security. The training is based on the 4th revised edition of the Advanced Windows Memory Dump Analysis with Data Structures book. It is also optionally containerized. The new version uses the latest WinDbg and includes additional scripting and memory topics.
Slides from the previous training sessions
Before the training, you get:
- Practical Foundations of Windows Debugging, Disassembling, Reversing, Second Edition PDF book (+300 pages)
- The current PDF book version
- The previous training recording
- Access to Software Diagnostics Library with more than 380 cross-referenced patterns of memory dump analysis, their classification, and more than 70 case studies
After the training, you also get:
- The new PDF book edition
- Personalized Certificate of Attendance with unique CID
- Optional Personalized Certificate of Completion with unique CID (after the tests)
- Answers to questions during training sessions
- Current training sessions recording
Prerequisites: Basic and intermediate level Windows memory dump analysis: the ability to list processors, processes, threads, modules, apply symbols, walk through stack traces and raw stack data, diagnose patterns such as heap corruption, CPU spike, memory leaks, access violation, wait chains and deadlocks. If you don't feel comfortable with prerequisites, then Accelerated Windows Memory Dump Analysis training or the corresponding book is recommended before attending this training.
Audience: Software technical support and escalation engineers, system administrators, security researchers, reverse engineers, malware and memory forensics analysts, software developers, and quality assurance engineers.
Book: Accelerated Windows Debugging 4D, Fourth Edition
Available in PDF format from Software Diagnostics Technology and Services.
The full transcript of Software Diagnostics Services training with 16 step-by-step exercises, notes, and source code of specially created modeling applications. Learn live local and remote debugging techniques in the kernel, user process, and managed .NET spaces using WinDbg debugger. The unique and innovative course teaches unified debugging patterns applied to real problems from complex software environments. The fourth edition was fully reworked and updated to use the latest WinDbg, added x64 disassembly review and Rust language to the existing and improved C/C++ and C# exercises.
Prerequisites: Working knowledge of one of these languages: C, C++, C#, Rust. Operating system internals and assembly language concepts are explained when necessary.
Audience: Software engineers, software maintenance engineers, escalation engineers, security and vulnerability researchers, malware and memory forensics analysts who want to learn live memory inspection techniques.
- Title: Accelerated Windows Debugging4: Training Course Transcript and WinDbg Practice Exercises, Fourth Edition
- Authors: Dmitry Vostokov, Software Diagnostics Services
- Publisher: OpenTask (February 2024)
- Language: English
- Product Dimensions: 28.0 x 21.6
- PDF: 372 pages
- ISBN-13: 978-1912636723

Defect Mechanism Patterns (DMP), Part 1
In 2015, we introduced patterns-based root cause analysis methodology by adding software problem mechanisms to accompany software diagnostic problems and their analysis patterns. We also planned to start populating the new pattern catalog at that time, but due to other developments and ideas, we have postponed it until now. We also plan to include a new pattern catalog and case studies in our modeling software defects course.
Usually, an identified software diagnostic problem may have several different mechanisms, and a mechanism may contribute to several diagnostic signs and symptoms. Knowing such mechanisms helps greatly in modeling a problem, devising a debugging strategy, and proposing a code fix.
We start with the Spiking Thread memory analysis pattern, which has concrete analysis pattern variants for Windows, Linux, and macOS.
From its Stack Trace, we may identify the source code location. If the code uses some memory-intensive data structure, we may have an instance of Inefficient Container Implementation. Another mechanism to consider is Partial Breaking Functionality. The defect mechanism pattern names are provisional and may change as more patterns are added that require name revisions for generality, consistency, and perhaps just better names.
Inefficient Container Implementation is when a wrong container or flawed implementation is used for memory and CPU-bound code. For example, using a contiguous vector instead of a linked list may affect CPU resource consumption on insertions and deletions. Some containers, such as queues, may use underlying container implementations that can be replaced.
Partial Breaking Functionality is when we have a potentially infinite loop with checks for some conditions that prevent it from running forever. However, the list of such conditions is only partially implemented, leaving some conditions unchecked, which causes a real infinite loop with the detected CPU consumption.
Carnot Cycle Metaphor for Trace and Log Analysis
Recently, we added a few “thermodynamic” analysis patterns to our trace and log analysis pattern catalog, such as Trace Volume, Trace Temperature, and, finally, derived from an ideal gas equation metaphor, Trace Pressure. These patterns allow us to employ a Carnot cycle metaphor for a typical analysis cycle:
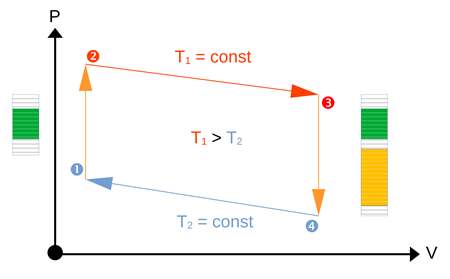
Initially, we have a low temperature (low importance) for a low volume of traces.
- During the incident, temperature (importance of traces) rises, triggering the rise in pressure.
- The volume of collected traces increases during investigations, and the pressure may go up or down.
- Once the problem is solved, the temperature comes down.
- During this phase, we do a retrospective and gradually reduce the volume of traces necessary for continuous monitoring to its original volume.
Online Training: Extended Windows Memory Dump Analysis

Software Diagnostics Services (PatternDiagnostics.com) organizes a training course:
August 5, 7, 12, 14, 19, 21, 2024, 7:00 pm - 9:00 pm (GMT+1) Price 99 USD Registration
Extended Windows Memory Dump Analysis: Using and Writing WinDbg Extensions, Database and Event Stream Processing, Visualization training course extends pattern-oriented analysis introduced in Accelerated Windows Memory Dump Analysis, Accelerated .NET Core Memory Dump Analysis, Advanced Windows Memory Dump Analysis with Data Structures, and Accelerated Windows Malware Analysis with Memory Dumps courses with elements of programming, data engineering, data science, and machine learning engineering:
- Surveying the current landscape of WinDbg extensions with analysis pattern mappings
- Writing WinDbg extensions in C, C++, and Rust (new)
- Connecting WinDbg to NoSQL databases
- Connecting WinDbg to streaming and log processing platforms
- Querying and visualizing WinDbg output data
- Using Machine Learning for diagnostics and postmortem debugging (new)
The new version of the training updates existing and includes new exercises.
Slides from the previous training
Before the training, you get:
- The current PDF book version and recording of the training
- Practical Foundations of Windows Debugging, Disassembling, Reversing, Second Edition PDF book
- Access to Software Diagnostics Library
After the training, you also get:
- The new edition of the PDF book version of the training
- Personalized Certificate of Attendance with unique CID
- Answers to questions during training sessions
- New recording
Prerequisites: Working knowledge of WinDbg. Working knowledge of Python, C, C++, or Rust is optional (required only for some exercises). Other concepts are explained when necessary.
Audience: Software developers, software maintenance engineers, escalation engineers, quality assurance engineers, security and vulnerability researchers, malware and memory forensics analysts who want to build memory analysis pipelines.
Online Training: Memory Thinking for Rust
Software Diagnostics Services organizes this online training course.

Memory Thinking for Rust training reviews memory-related topics from the perspective of software structure and behavior analysis and teaches Rust language aspects in parallel while demonstrating relevant code internals using WinDbg and GDB on Windows (x64) and Linux (x64 and ARM64) platforms:
- a tour of relevant language constructs
- memory layout of structures
- references, borrowing, and lifecycle
- local, static, and dynamic memory
- generics
- functions
- object-oriented and functional programming
- multithreading and synchronization
- unsafe code
- Windows and Linux specifics
- … and much more
April 22, 24, May 1, 8, 15, 2024, 7:00 pm - 8:00 pm (GMT+1) Price 99 USD Registration
System programming on Windows and Linux using Rust is unthinkable without OS API. To avoid repeating some topics and save time, the training includes the Accelerated Windows and Linux API for Software Diagnostics books as a follow-up or additional references. A necessary x64 and ARM64 review for some topics is also included.
Before the training, you get:
- Accelerated Linux API for Software Diagnostics (+300 pages)
- Accelerated Windows API for Software Diagnostics (+200 pages)
- Access to Software Diagnostics Library with more than 370 cross-referenced patterns of memory dump analysis, their classification, and more than 70 case studies
After the training, you also get:
- The training PDF book edition
- Personalized Certificate of Attendance with unique CID
- Answers to questions during training sessions
- Recording
Online Training: Accelerated C & C++ for Windows Diagnostics
Software Diagnostics Services organizes this online training course.

For approximate training content, please see the first 40 slides (there are more than 200 slides in total) and TOC from the corresponding Memory Thinking book.
Solid C and C++ knowledge is a must to fully understand Windows diagnostic artifacts such as memory dumps and do diagnostic, forensic, and root cause analysis beyond listing stack traces, DLL, and driver information. C and C++ for Windows Software Diagnostics training reviews the following topics from the perspective of software structure and behavior analysis and teaches C and C++ languages in parallel:
- a tour of relevant language(s) constructs - classic/legacy C++, C++11, and later standards
- Windows specifics
- pointers and references
- memory layout of structures and objects
- local, static, and dynamic memory
- object lifecycle
- standard library
- compilation, static and dynamic linkage
- multithreading and synchronization
- bad and insecure code
- … and more
System and desktop application programming on Windows using C and C++ is unthinkable without Windows API. To avoid repeating some topics and save time, the training includes the Accelerated Windows API for Software Diagnostics book as a follow-up or additional reference. There is also a necessary x64 review for some topics, but if you are never used to reading assembly language, Practical Foundations of Windows Debugging, Disassembling, Reversing book is also included.
Before the training, you get the following:
- Memory Thinking for C & C++ Windows Diagnostics PDF book (250 pages)
- Practical Foundations of Windows Debugging, Disassembling, Reversing, Second Edition PDF book (+300 pages)
- Accelerated Windows API for Software Diagnostics PDF book (+300 pages)
- Access to Software Diagnostics Library with more than 370 cross-referenced patterns of memory dump analysis, their classification, and more than 70 case studies
After the training, you also get the following:
- The revised Memory Thinking PDF book of the training
- Personalized Certificate of Attendance with unique CID
- Answers to questions during training sessions
- Recording
Online Training: Accelerated Rust Windows Memory Dump Analysis
Software Diagnostics Services organizes this online training course.

This training includes step-by-step exercises and covers dozens of crash dump analysis patterns from the x64 process, kernel, and complete (physical) memory dumps. Learn how to analyze Rust applications, services, and system crashes and freezes, navigate through memory dump space, and diagnose heap corruption, memory leaks, CPU spikes, blocked threads, deadlocks, wait chains, and much more with WinDbg debugger. The training uses a unique and innovative pattern-oriented analysis approach developed by the Software Diagnostics Institute to speed up the learning curve, and it is structurally based on the latest 6th revised edition of the bestselling Accelerated Windows Memory Dump Analysis book with the focus on safe and unsafe Rust code and its interfacing with the Windows OS. The training is useful whether you come to Rust from C and C++ or interpreted languages like Python and facilitates memory thinking when programming in Rust.
September 23 - 26, 2024, 7:00 pm - 8:30 pm (GMT+1) Price 99 USD Registration
Before the training, you get:
- Practical Foundations of Windows Debugging, Disassembling, Reversing, Second Edition PDF book (+300 pages)
- Access to Software Diagnostics Library with more than 370 cross-referenced patterns of memory dump analysis, their classification, and more than 70 case studies
After the training, you also get:
- The training PDF book edition
- Personalized Certificate of Attendance with unique CID
- Optional Personalized Certificate of Completion with unique CID (after the tests)
- Answers to questions during training sessions
- Current training sessions recording
Prerequisites: Basic Windows troubleshooting.
Audience: Software technical support and escalation engineers, system administrators, security and vulnerability researchers, reverse engineers, malware and memory forensics analysts, DevSecOps and SRE, software developers, system programmers, and quality assurance engineers.
Slides from the structurally similar C and C++ training version, Part 1
Slides from the structurally similar C and C++ training version, Part 2
If you are mainly interested in C and C++ Windows memory dump analysis, there is another training: Accelerated Windows Memory Dump Analysis
If you are mainly interested in .NET memory dump analysis, there is another training: Accelerated .NET Core Memory Dump Analysis
If you are interested in C and C++ Linux memory dump analysis, there is another training: Accelerated Linux Core Dump Analysis
Memory Thinking for C & C++ Linux Diagnostics
Available in PDF format from Software Diagnostics Services
Solid C and C++ knowledge is a must to fully understand Linux diagnostic artifacts such as core memory dumps and do diagnostic, forensic, and root cause analysis beyond listing backtraces. This full-color reference book is a part of the Accelerated C & C++ for Linux Diagnostics training course organized by Software Diagnostics Services. The text contains slides, brief notes highlighting particular points, and replicated source code fragments that are easy to copy into your favorite IDE. The book's detailed Table of Contents makes the usual Index redundant. We hope this reference is helpful for the following audiences:
- C and C++ developers who want to deepen their knowledge
- Software engineers developing and maintaining products on Linux platforms
- Technical support, escalation, DevSecOps, cloud and site reliability engineers dealing with complex software issues
- Quality assurance engineers who test software on Linux platforms
- Security and vulnerability researchers, reverse engineers, malware and memory forensics analysts

- Title: Memory Thinking for C & C++ Linux Diagnostics: Slides with Descriptions Only
- Authors: Dmitry Vostokov, Software Diagnostics Services, Dublin School of Security
- Language: English
- Product Dimensions: 21.6 x 14.0
- PDF: 258 pages
- Publisher: OpenTask (December 2023)
- ISBN-13: 978-1912636570
Memory Thinking for C & C++ Windows Diagnostics
Available in PDF format from Software Diagnostics Services
Solid C and C++ knowledge is a must to fully understand Windows diagnostic artifacts such as memory dumps and do diagnostic, forensic, and root cause analysis beyond listing stack traces, DLL, and driver information. This full-color reference book is a part of the Accelerated C & C++ for Windows Diagnostics training course organized by Software Diagnostics Services. The text contains slides, brief notes highlighting particular points, and replicated source code fragments that are easy to copy into your favorite IDE. The book's detailed Table of Contents makes the usual Index redundant. We hope this reference is helpful for the following audiences:
- C and C++ developers who want to deepen their knowledge
- Software engineers developing and maintaining products on Windows platforms
- Technical support, escalation, DevSecOps, cloud and site reliability engineers dealing with complex software issues
- Quality assurance engineers who test software on Windows platforms
- Security and vulnerability researchers, reverse engineers, malware and memory forensics analysts

- Title: Memory Thinking for C & C++ Windows Diagnostics: Slides with Descriptions Only
- Authors: Dmitry Vostokov, Software Diagnostics Services, Dublin School of Security
- Language: English
- Product Dimensions: 21.6 x 14.0
- PDF: 250 pages
- Publisher: OpenTask (November 2023)
- ISBN-13: 978-1912636730
Accelerated Windows Memory Dump Analysis, Sixth Edition, Part 2: Kernel and Complete Spaces
The following direct links can be used to order the book:
Buy PDF from Leanpub
Buy Kindle edition
Also available in PDF format from Software Diagnostics Services
The full-color transcript of Software Diagnostics Services training sessions with 14 step-by-step exercises, notes, source code of specially created modeling applications, and 45 questions and answers. Covers more than 35 crash dump analysis patterns from x64 kernel and complete (physical) memory dumps. Learn how to analyze system crashes and freezes, navigate through the kernel and complete spaces, and diagnose patterns of abnormal software behavior with WinDbg debugger. The training uses a unique and innovative pattern-oriented analysis approach developed by Software Diagnostics Institute to speed up the learning curve. Prerequisites: Basic Windows troubleshooting. Audience: Software technical support and escalation engineers, system administrators, security researchers, reverse engineers, malware and memory forensics analysts, software developers and quality assurance engineers, and site reliability engineers. The 6th edition was fully reworked for the latest WinDbg version and includes additional relevant x64 assembly language review and BSOD analysis pattern strategy outline.
- Title: Accelerated Windows Memory Dump Analysis, Sixth Edition, Part 2, Kernel and Complete Spaces: Training Course Transcript and WinDbg Practice Exercises with Notes
- Authors: Dmitry Vostokov, Software Diagnostics Services
- Publisher: OpenTask (August 2023)
- Language: English
- PDF: 388 pages
- ISBN-13: 978-1912636938

Accelerated Windows Memory Dump Analysis, Sixth, Part 1: Process User Space
The following direct links can be used to order the book now:
Buy PDF from Leanpub
Buy Kindle edition
Also available in PDF format from Software Diagnostics Services
The full-color transcript of Software Diagnostics Services training sessions with 22 step-by-step exercises, notes, source code of specially created modeling applications, and more than 70 questions and answers. Covers more than 50 crash dump analysis patterns from x86 and x64 process memory dumps. Learn how to analyze application and service crashes and freezes, navigate through process user space, and diagnose heap corruption, memory and handle leaks, CPU spikes, blocked threads, deadlocks, wait chains, and many more patterns of abnormal software behavior with WinDbg debugger. The training uses a unique and innovative pattern-oriented analysis approach developed by Software Diagnostics Institute to speed up the learning curve. Prerequisites: Basic Windows troubleshooting. Audience: Software technical support and escalation engineers, system administrators, security researchers, reverse engineers, malware and memory forensics analysts, software developers and quality assurance engineers, and site reliability engineers. The 6th edition was fully reworked for the latest WinDbg version and includes additional Windows 11 memory dumps, relevant x64 assembly language review, and a Rust memory dump analysis example.
- Title: Accelerated Windows Memory Dump Analysis, Sixth Edition, Part 1, Process User Space: Training Course Transcript and WinDbg Practice Exercises with Notes
- Authors: Dmitry Vostokov, Software Diagnostics Services
- Publisher: OpenTask (August 2023)
- Language: English
- Paperback: 354 pages
- ISBN-13: 978-1912636921

Book: Accelerated Disassembly, Reconstruction and Reversing, Third Edition
The following direct links can be used to order the book now:
Buy PDF from Leanpub
Buy Kindle edition
Available in PDF format from Software Diagnostics Services.
The original first edition is available for SkillSoft Books24x7 subscribers
The book contains the full transcript of Software Diagnostics Services training. Learn disassembly, execution history reconstruction, and binary reversing techniques for better software diagnostics, troubleshooting, debugging, memory forensics, vulnerability, and malware analysis on x64 Windows platforms. The course uses a unique and innovative pattern-oriented analysis approach to speed up the learning curve. The training consists of practical step-by-step, hands-on exercises using WinDbg and memory dumps. Covered more than 25 ADDR patterns, and many concepts are illustrated with Memory Cell Diagrams. The prerequisites for this training are working knowledge of C and C++ programming languages. Operating system internals and assembly language concepts are explained when necessary. The primary audience for this training is software technical support and escalation engineers who analyze memory dumps from complex software environments and need to go deeper in their analysis of abnormal software structure and behavior. The course is also useful for software engineers, quality assurance and software maintenance engineers who debug software running on diverse computer environments, security researchers, malware, and memory forensics analysts who have never used WinDbg for analysis of computer memory. The third edition includes the x64 disassembly review and internals of C++ virtual function calls.
- Title: Accelerated Disassembly, Reconstruction and Reversing: Training Course Transcript and WinDbg Practice Exercises with Memory Cell Diagrams, Third Edition
- Authors: Dmitry Vostokov, Software Diagnostics Services
- Publisher: OpenTask (September 2023)
- Language: English
- Product Dimensions: 28.0 x 21.6
- PDF: 269 pages
- ISBN-13: 978-1912636679

Table of Contents and sample exercise
Slides from the training
Accelerated Linux Disassembly, Reconstruction and Reversing, Second Edition
The following direct links can be used to order the book now:
Buy PDF from Leanpub
Buy Kindle edition
Also available in PDF and recording formats from Software Diagnostics Services.
The book contains the full transcript of Software Diagnostics Services training. Learn disassembly, execution history reconstruction, and binary reversing techniques for better software diagnostics, troubleshooting, debugging, memory forensics, vulnerability and malware analysis on x64 (x86_64) and A64 (ARM64, AArch64) Linux platforms. The course uses a unique and innovative pattern language approach to speed up the learning curve. The training consists of practical step-by-step, hands-on exercises using GDB and Linux core memory dumps. Covered more than 25 ADDR patterns originally introduced for the x64 Windows platform, and many concepts are illustrated with Memory Cell Diagrams. The prerequisites for this training are working knowledge of C and C++ programming languages. Operating system internals and assembly language concepts are explained when necessary. The primary audience for this training is software technical support and escalation engineers who analyze memory dumps from complex software environments and need to go deeper in their analysis of abnormal software structure and behavior. The course is also useful for software engineers, quality assurance and software maintenance engineers who debug software running on diverse cloud and endpoint computer environments, SRE and DevSecOps, security and vulnerability researchers, malware and memory forensics analysts who have never used GDB for analysis of computer memory. The book also features ADDR pattern descriptions summarized after each exercise. The second edition includes a review of relevant assembly language fundamentals and relevant differences between GCC and Clang.
- Title: Accelerated Linux Disassembly, Reconstruction and Reversing: Training Course Transcript and GDB Practice Exercises with Memory Cell Diagrams, Second Edition
- Authors: Dmitry Vostokov, Software Diagnostics Services
- Publisher: OpenTask (March 2023)
- Language: English
- Product Dimensions: 28.0 x 21.6
- PDF: 282 pages
- ISBN-13: 978-1912636747

Table of Contents and sample exercise
Slides from the training
An Introduction to Malware Narratives, Revised Edition
The following direct links can be used to order the book now:
Buy PDF from Leanpub
Buy Kindle version
Buy Paperback from Amazon (previous edition)
from Amazon (previous edition)
Buy Paperback from Barnes & Noble (previous edition)
The previous edition is also available for SkillSoft Books24x7 subscribers
Software Narratology, the science of software stories, found its successful application in software diagnostics of abnormal software behavior, especially in the pattern-oriented analysis of software logs from complex systems with millions of events, thousands of threads, hundreds of processes and modules. This is a revised and updated transcript of the Software Diagnostics Services seminar on the new application of software narratology to malware analysis.
- Title: Malware Narratives: An Introduction, Revised Edition
- Authors: Dmitry Vostokov, Software Diagnostics Services
- Publisher: OpenTask (October 2023)
- Language: English
- Product Dimensions: 28.0 x 21.6
- Paperback: 55 pages
- ISBN-13: 978-1912636525

Introducing Lov Language

In the past, I paid little attention to traditional performance and system behavior visualizations, for example, for time series. My own visualizations included Dia|gram graphical language for software narratives such as traces and logs and, recently, memory snapshots. My latest exposure to open-source observability and visualization tools led me to think about how to describe patterns I see in a pattern language. It is easy to communicate what I see by just sending the picture, but often, we need to compare it to the previous observations or do some symbolic processing of such information.
I decided to tailor existing rich diagnostic analysis pattern languages I developed over the last +15 years into the Language of visualizations that I simply call the Lov language, my new old love of visualizations of software behavior (no pun intended). It is not a programming language but primarily a language for description and analysis; also, it can be used for hypothesis testing and simulation with the appropriate tool support. The initial inspiration for Lov comes from two dual activities: visualization synthesis for time series data and analysis of such visualizations. For a simple initial illustration, the visualization description above of CPU consumption for all processes in the system reuses the existing Discontinuity for all PID Adjoint Threads of Activity and Blackout trace and log analysis patterns. We also see Signals for Counter Values. More Lov to come in the forthcoming months.
Online Training: Accelerated Windows Debugging 5D

Software Diagnostics Services (PatternDiagnostics.com) organizes a training course:
Learn live local and remote debugging techniques and tricks in the kernel, user process, and managed .NET spaces using the WinDbg debugger. The unique and innovative Debugging5 course teaches unified debugging patterns applied to real problems from complex software environments. The training consists of practical, step-by-step, hands-on exercises. The new edition extends the previous version with the additional discussion of the pattern-oriented debugging process and the unified debugging patterns, uses the latest WinDbg, and adds Rust language to the existing C/C++ and C# exercises.
Slides from the previous Debugging4 training
Before the training, you get:
- Practical Foundations of Windows Debugging, Disassembling, Reversing, Second Edition PDF book
- Accelerated Windows Debugging4 PDF book
- Access to Software Diagnostics Library
After the training, you also get the following:
- The new edition of the PDF book version of the training
- Personalized Certificate of Attendance with unique CID
- Answers to questions during training sessions
- Recording
Prerequisites: Working knowledge of one of these languages: C, C++, C#, Rust. Operating system internals and assembly language concepts are explained when necessary.
Audience: software engineers, software maintenance engineers, escalation engineers, security and vulnerability researchers, malware and memory forensics analysts who want to learn live memory inspection techniques.
If you are interested in Windows postmortem software diagnostics using memory dump files, there are other courses available:
Accelerated Windows Memory Dump Analysis
Accelerated .NET Core Memory Dump Analysis
Online Training: Accelerated Windows Disassembly, Reconstruction and Reversing
Software Diagnostics Services organizes this online training course.

Learn disassembly, execution history reconstruction, and binary reversing techniques for better software diagnostics, troubleshooting, and debugging on x64 Windows platforms. The course uses a unique and innovative pattern-oriented analysis approach to speed up the learning curve. The training consists of practical step-by-step, hands-on exercises using WinDbg and memory dumps. Covered more than 25 ADDR patterns, and many concepts are illustrated with Memory Cell Diagrams. The prerequisites for this training are working knowledge of C and C++ programming languages. Operating system internals and assembly language concepts are explained when necessary. The primary audience for this training is software technical support and escalation engineers who analyze memory dumps from complex software environments and need to go deeper in their analysis of abnormal and malicious software structure and behavior. The course is also useful for software engineers, quality assurance and software maintenance engineers who debug software running on diverse cloud and endpoint computer environments, security and vulnerability researchers, and malware and memory forensics analysts who have never used WinDbg for analysis of computer memory. The course builds upon and extends the basic patterns introduced in the Practical Foundations of Windows Debugging, Disassembling, Reversing book. The new version includes an overview of the relevant x64 assembly language.
Slides from the previous training
Before the training, you get:
- Practical Foundations of Windows Debugging, Disassembling, Reversing, Second Edition PDF book
- The previous PDF book version of the training
- Access to Software Diagnostics Library
After the training, you also get:
- The new 2nd edition PDF book of the training
- Personalized Certificate of Attendance with unique CID
- Optional Personalized Certificate of Completion with unique CID (after the tests)
- Answers to questions during training sessions
- Recording
Online Training: Accelerated Windows Memory Dump Analysis
Software Diagnostics Services organizes this online training course.

Slides from the previous training version, days 1-3
Slides from the previous training version, days 4-6
New dates/times TBD
This training includes 32 step-by-step exercises and covers more than 65 crash dump analysis patterns from x86 and x64 process, kernel, and complete (physical) memory dumps. Learn how to analyze application, service and system crashes and freezes, navigate through memory dump space and diagnose heap corruption, memory leaks, CPU spikes, blocked threads, deadlocks, wait chains, and much more with WinDbg debugger. The training uses a unique and innovative pattern-oriented analysis approach developed by Software Diagnostics Institute to speed up the learning curve, and it is based on the latest 5th revised edition of the bestselling Accelerated Windows Memory Dump Analysis book. This new training version also includes:
- x86 and x64 disassembly overviews
- Additional memory analysis patterns
- Memory dump analysis of Go and Rust processes
- Additional coverage of BSOD
- New kernel exercises with source code
Training outline:
- Day 1 (2 hours): Overview. Process memory dump analysis.
- Day 2 (2 hours): Process memory dump analysis.
- Day 3 (2 hours): Process memory dump analysis.
- Day 4 (2 hours): Kernel memory dump analysis.
- Day 5 (2 hours): Complete (physical) memory dump analysis.
- Day 6 (2 hours): Additional memory dump analysis topics.
Before the training, you get:
- Practical Foundations of Windows Debugging, Disassembling, Reversing, Second Edition PDF book (+300 pages)
- The current PDF book version (+700 pages)
- The previous training recording
- Access to Software Diagnostics Library with more than 370 cross-referenced patterns of memory dump analysis, their classification, and more than 70 case studies
After the training, you also get:
- The new 6th PDF book edition (+800 pages)
- Personalized Certificate of Attendance with unique CID
- Optional Personalized Certificate of Completion with unique CID (after the tests)
- Answers to questions during training sessions
- Current training sessions recording
Prerequisites: Basic Windows troubleshooting
Audience: Software technical support and escalation engineers, system administrators, security and vulnerability researchers, reverse engineers, malware and memory forensics analysts, DevSecOps and SRE, software developers, and quality assurance engineers.
If you are mainly interested in .NET memory dump analysis, there is another training: Accelerated .NET Core Memory Dump Analysis
If you are interested in Linux memory dump analysis, there is another training: Accelerated Linux Core Dump Analysis
Book: Accelerated Linux API for Software Diagnostics
Available in PDF format from Software Diagnostics Services.
The book contains the full transcript of Software Diagnostics Services training with 16 hands-on exercises.
Knowledge of Linux API is necessary for:
- Development
- Malware analysis
- Vulnerability analysis and exploitation
- Reversing
- Diagnostics
- Debugging
- Memory forensics
- Crash and hang analysis
- Secure coding
- Static code analysis
- Trace and log analysis
The training uses a unique and innovative pattern-oriented analysis approach and provides:
- Overview
- Classification
- Patterns
- Internals
- Development examples
- Analysis examples
- Comparison with Windows API

- Title: Accelerated Linux API for Software Diagnostics: With Category Theory in View
- Authors: Dmitry Vostokov, Software Diagnostics Services
- Publisher: OpenTask (June 2023)
- Language: English
- Product Dimensions: 28.0 x 21.6
- PDF: 232 pages
- ISBN-13: 978-1912636624
Table of Contents and sample exercise
Slides from the training
Runtime Thread (Python, Linux)
We continue extending our memory analysis pattern language to Python execution environment after introducing Managed Stack Trace variant. Now we add Runtime Thread (former CLR Thread memory analysis pattern) variant. For Linux and GDB, in the case of Reduced Symbolic Information we get this stack trace:
(gdb) bt
#0 0x00007ffff7caeb97 in __GI___select (nfds=0, readfds=0x0, writefds=0x0, exceptfds=0x0, timeout=0x7fffffffd9f0)
at ../sysdeps/unix/sysv/linux/select.c:41
#1 0x00000000004e8965 in ?? ()
#2 0x00000000005d8711 in _PyMethodDef_RawFastCallKeywords ()
#3 0x000000000054b330 in ?? ()
#4 0x00000000005524cd in _PyEval_EvalFrameDefault ()
#5 0x00000000005d91fc in _PyFunction_FastCallKeywords ()
#6 0x000000000054e5ac in _PyEval_EvalFrameDefault ()
#7 0x00000000005d91fc in _PyFunction_FastCallKeywords ()
#8 0x000000000054e5ac in _PyEval_EvalFrameDefault ()
#9 0x00000000005d91fc in _PyFunction_FastCallKeywords ()
#10 0x000000000054e5ac in _PyEval_EvalFrameDefault ()
#11 0x000000000054bcc2 in _PyEval_EvalCodeWithName ()
#12 0x000000000054e0a3 in PyEval_EvalCode ()
#13 0x0000000000630ce2 in ?? ()
#14 0x0000000000630d97 in PyRun_FileExFlags ()
#15 0x00000000006319ff in PyRun_SimpleFileExFlags ()
#16 0x000000000065432e in ?? ()
#17 0x000000000065468e in _Py_UnixMain ()
#18 0x00007ffff7be209b in __libc_start_main (main=0x4bc560 <main>, argc=2, argv=0x7fffffffe4c8, init=<optimized out>, fini=<optimized out>,
rtld_fini=<optimized out>, stack_end=0x7fffffffe4b8) at ../csu/libc-start.c:308
#19 0x00000000005e0e8a in _start ()
If we install python debug package (for example, python3.7-dbg) we get full symbolic information:
(gdb) bt
#0 0x00007ffff7caeb97 in __GI___select (nfds=0, readfds=0x0, writefds=0x0, exceptfds=0x0, timeout=0x7fffffffd9f0)
at ../sysdeps/unix/sysv/linux/select.c:41
#1 0x00000000004e8965 in pysleep (secs=<optimized out>) at ../Modules/timemodule.c:1829
#2 time_sleep (self=<optimized out>, obj=<optimized out>, self=<optimized out>, obj=<optimized out>) at ../Modules/timemodule.c:371
#3 0x00000000005d8711 in _PyMethodDef_RawFastCallKeywords (method=0x82dbe0 <time_methods+288>, self=<module at remote 0x7ffff77d5c28>,
args=0x7ffff788c550, nargs=<optimized out>, kwnames=<optimized out>) at ../Objects/call.c:644
#4 0x000000000054b330 in _PyCFunction_FastCallKeywords (kwnames=<optimized out>, nargs=<optimized out>, args=0x7ffff788c550,
func=<built-in method sleep of module object at remote 0x7ffff77d5c28>) at ../Objects/call.c:730
#5 call_function (pp_stack=0x7fffffffdb60, oparg=<optimized out>, kwnames=<optimized out>) at ../Python/ceval.c:4568
#6 0x00000000005524cd in _PyEval_EvalFrameDefault (f=<optimized out>, throwflag=<optimized out>) at ../Python/ceval.c:3093
#7 0x00000000005d91fc in PyEval_EvalFrameEx (throwflag=0, f=Frame 0x7ffff788c3d8, for file sleepLoop.py, line 11, in bar ()) at ../Python/ceval.c:547
#8 function_code_fastcall (globals=<optimized out>, nargs=<optimized out>, args=<optimized out>, co=<optimized out>) at ../Objects/call.c:283
#9 _PyFunction_FastCallKeywords (func=<optimized out>, stack=<optimized out>, nargs=<optimized out>, kwnames=<optimized out>) at ../Objects/call.c:408
#10 0x000000000054e5ac in call_function (kwnames=0x0, oparg=<optimized out>, pp_stack=<synthetic pointer>) at ../Python/ceval.c:4616
#11 _PyEval_EvalFrameDefault (f=<optimized out>, throwflag=<optimized out>) at ../Python/ceval.c:3124
#12 0x00000000005d91fc in PyEval_EvalFrameEx (throwflag=0, f=Frame 0x7ffff77d85e8, for file sleepLoop.py, line 7, in foo ()) at ../Python/ceval.c:547
#13 function_code_fastcall (globals=<optimized out>, nargs=<optimized out>, args=<optimized out>, co=<optimized out>) at ../Objects/call.c:283
#14 _PyFunction_FastCallKeywords (func=<optimized out>, stack=<optimized out>, nargs=<optimized out>, kwnames=<optimized out>) at ../Objects/call.c:408
#15 0x000000000054e5ac in call_function (kwnames=0x0, oparg=<optimized out>, pp_stack=<synthetic pointer>) at ../Python/ceval.c:4616
#16 _PyEval_EvalFrameDefault (f=<optimized out>, throwflag=<optimized out>) at ../Python/ceval.c:3124
#17 0x00000000005d91fc in PyEval_EvalFrameEx (throwflag=0, f=Frame 0x926ee8, for file sleepLoop.py, line 4, in main ()) at ../Python/ceval.c:547
#18 function_code_fastcall (globals=<optimized out>, nargs=<optimized out>, args=<optimized out>, co=<optimized out>) at ../Objects/call.c:283
#19 _PyFunction_FastCallKeywords (func=<optimized out>, stack=<optimized out>, nargs=<optimized out>, kwnames=<optimized out>) at ../Objects/call.c:408
#20 0x000000000054e5ac in call_function (kwnames=0x0, oparg=<optimized out>, pp_stack=<synthetic pointer>) at ../Python/ceval.c:4616
#21 _PyEval_EvalFrameDefault (f=<optimized out>, throwflag=<optimized out>) at ../Python/ceval.c:3124
#22 0x000000000054bcc2 in PyEval_EvalFrameEx (throwflag=0, f=Frame 0x7ffff78739f8, for file sleepLoop.py, line 14, in <module> ())
at ../Python/ceval.c:547
#23 _PyEval_EvalCodeWithName (_co=<optimized out>, globals=<optimized out>, locals=<optimized out>, args=<optimized out>, argcount=<optimized out>,
kwnames=0x0, kwargs=0x0, kwcount=<optimized out>, kwstep=2, defs=0x0, defcount=0, kwdefs=0x0, closure=0x0, name=0x0, qualname=0x0)
at ../Python/ceval.c:3930
#24 0x000000000054e0a3 in PyEval_EvalCodeEx (closure=0x0, kwdefs=0x0, defcount=0, defs=0x0, kwcount=0, kws=0x0, argcount=0, args=0x0,
locals=<optimized out>, globals=<optimized out>, _co=<optimized out>) at ../Python/ceval.c:3959
#25 PyEval_EvalCode (co=<optimized out>, globals=<optimized out>, locals=<optimized out>) at ../Python/ceval.c:524
#26 0x0000000000630ce2 in run_mod (mod=<optimized out>, filename=<optimized out>,
globals={'__name__': '__main__', '__doc__': None, '__package__': None, '__loader__': <SourceFileLoader(name='__main__', path='sleepLoop.py') at remote 0x7ffff7805f60>, '__spec__': None, '__annotations__': {}, '__builtins__': <module at remote 0x7ffff78cac28>, '__file__': 'sleepLoop.py', '__cached__': None, 'time': <module at remote 0x7ffff77d5c28>, 'main': <function at remote 0x7ffff78411e0>, 'foo': <function at remote 0x7ffff7731c80>, 'bar': <function at remote 0x7ffff7731d08>},
locals={'__name__': '__main__', '__doc__': None, '__package__': None, '__loader__': <SourceFileLoader(name='__main__', path='sleepLoop.py') at remote 0x7ffff7805f60>, '__spec__': None, '__annotations__': {}, '__builtins__': <module at remote 0x7ffff78cac28>, '__file__': 'sleepLoop.py', '__cached__': None, 'time': <module at remote 0x7ffff77d5c28>, 'main': <function at remote 0x7ffff78411e0>, 'foo': <function at remote 0x7ffff7731c80>, 'bar': <function at remote 0x7ffff7731d08>}, flags=<optimized out>, arena=<optimized out>) at ../Python/pythonrun.c:1035
#27 0x0000000000630d97 in PyRun_FileExFlags (fp=0x92e490, filename_str=<optimized out>, start=<optimized out>,
globals={'__name__': '__main__', '__doc__': None, '__package__': None, '__loader__': <SourceFileLoader(name='__main__', path='sleepLoop.py') at remote 0x7ffff7805f60>, '__spec__': None, '__annotations__': {}, '__builtins__': <module at remote 0x7ffff78cac28>, '__file__': 'sleepLoop.py', '__cached__': No--Type <RET> for more, q to quit, c to continue without paging--
ne, 'time': <module at remote 0x7ffff77d5c28>, 'main': <function at remote 0x7ffff78411e0>, 'foo': <function at remote 0x7ffff7731c80>, 'bar': <function at remote 0x7ffff7731d08>},
locals={'__name__': '__main__', '__doc__': None, '__package__': None, '__loader__': <SourceFileLoader(name='__main__', path='sleepLoop.py') at remote 0x7ffff7805f60>, '__spec__': None, '__annotations__': {}, '__builtins__': <module at remote 0x7ffff78cac28>, '__file__': 'sleepLoop.py', '__cached__': None, 'time': <module at remote 0x7ffff77d5c28>, 'main': <function at remote 0x7ffff78411e0>, 'foo': <function at remote 0x7ffff7731c80>, 'bar': <function at remote 0x7ffff7731d08>}, closeit=1, flags=0x7fffffffe2ac) at ../Python/pythonrun.c:988
#28 0x00000000006319ff in PyRun_SimpleFileExFlags (fp=0x92e490, filename=<optimized out>, closeit=1, flags=0x7fffffffe2ac) at ../Python/pythonrun.c:429
#29 0x000000000065432e in pymain_run_file (p_cf=0x7fffffffe2ac, filename=<optimized out>, fp=0x92e490) at ../Modules/main.c:427
#30 pymain_run_filename (cf=0x7fffffffe2ac, pymain=0x7fffffffe380) at ../Modules/main.c:1627
#31 pymain_run_python (pymain=0x7fffffffe380) at ../Modules/main.c:2877
#32 pymain_main (pymain=<optimized out>, pymain=<optimized out>) at ../Modules/main.c:3038
#33 0x000000000065468e in _Py_UnixMain (argc=<optimized out>, argv=<optimized out>) at ../Modules/main.c:3073
#34 0x00007ffff7be209b in __libc_start_main (main=0x4bc560 <main>, argc=2, argv=0x7fffffffe4c8, init=<optimized out>, fini=<optimized out>,
rtld_fini=<optimized out>, stack_end=0x7fffffffe4b8) at ../csu/libc-start.c:308
#35 0x00000000005e0e8a in _start () at ../Modules/main.c:797



















